
NewsletterSeptember 2012Newsletter Editor: In This Issue:
Meeting information
Future Meetings: (subject to change)
Do not forget to bring your used ink cartridges. Minutes of the August 2012 Meetingby Penny Holland, Secretary The August monthly meeting of MAGIC took place at the Unitarian Congregation Meeting House in Freeland from 4 to 6 PM on Wednesday, August 15. BUSINESS MEETING Following Robert's first hour of Q and A, the business portion of the meeting was led by President Sue Keblusek. She announced that MAGIC donated our old (and no longer used) projector to Whidbey Commons where people will have access to its use in the back room. Another announcement is that MAGIC is in the process of giving money to the 4H group which, led by Robert Elphick, is putting on their earthquake preparedness video show this weekend at the Whidbey Island Area Fair. Our MAGIC group has been promised a viewing at a later date. Treasury Report: In Bonnieʼs absence, President Sue stated that we have a balance of $4,530.67. The need for someone to collect inkjet cartridges for recycle resulted in a new volunteer stepping forward. Member Paul Morris has kindly consented to take over this task. Thank you Paul. One last announcement regarded the set up and take down of chairs and/or tables at our meeting place. It turns out that our president has been doing a lot of the set up prior to the meetings, and we have told her that is not her job. We are asking members try to arrive ten minutes or so early to help set up tables, rearrange chairs and cover the front windows. At the end of the meeting it has not been such a problem, as there have always been people who help put the tables away. Thanks, everyone, for your help in this matter! PROGRAM Robert Elphick gave this monthʼs presentation on the latest Mac Operating System, known as Mountain Lion. He demonstrated a number of the new features that have come along with Lion and especially Mountain Lion, both of which have been developed to more closely align with the looks and workings of the iPad, iPhone, etc. He talked about the Alerts and Notifications, Reminders, and Notes (which used to be part of Mail but is now a separate program .) Other new features he discussed were Sharing, Power Nap, and Launch Pad. But probably the one that got the most oohs and ahs was Dictation and Speech which Robert demonstrated by speaking a few sentences, which amazingly appeared a few seconds later as typed text on the screen, with but a few errors! Regarding switching to Mountain Lion, people are advised to do their homework first. There is a rather detailed section on the MAGIC website, see MAGIC Newsletter June 2011, titled "Prepare for Lion" which should be checked out to determine which programs will transfer, and which versions of the Mac are compatible. Tom Johnson also suggested that people take a look at some of the Apple Forums on the subject. Apparently there are some horror stories being told, so "buyer beware!" MAGIC Editors note: The "horror stories" have basically been people starting iCloud accounts, then deciding to opt out. When quitting the iCloud account, your information is deleted and syncs to all your devices, so your information is deleted off all your devices as well. If you are not sure about iCloud, do not set up an iCloud account and there should be no problems. For more information, also see Lion, Mountain Lion, & iCloud. 
MAGIC Momentsby RYE Earthquake DocumentaryMAGIC has been sponsoring the 4-HD Video Club led by yours truly. The club has completed an ambitious project to provide a documentary to help residents of Whidbey Island to prepare for a major earthquake. The documentary contains a lot of interesting geophysics that explains the risks as well as a lot of information about how to prepare and how the county will respond to any earthquake emergency. The documentary will be shown at the beginning of the September monthly meeting. Bring friends and relatives to see this important documentary. MAGIC has decided to award a donation to the 4-HD Video Club to help offset the expenses of making the movie. The check will be awarded to one of the kids who made the documentary at the meeting.SOFTWARE UPDATESNote: This Software Update section of the newsletter lists the most relevant Apple updates. Not all updates are listed for all products. Additionally, I'll add other pertinent updates on occasion. Apple plugs Java hole, shifts away from plug-inby Antone Gonsalves, csoonline.com - Sep 7, 2012 
Apple has released a fix for a critical Java vulnerability, while also taking further steps to distance itself from the technology, which has become a major security risk in Web browsers. Apple released the fix Wednesday for Mac OS X Snow Leopard, Lion and Mountain Lion. The patches, Java for Mac OS X 10.6 Update 10 and Java for OS X 2012-005, shipped a week after Java-steward Oracle released an emergency patch. As as of this week, more than a quarter-million computers on the Web have been infected with malware exploiting the vulnerabilities, said Atif Mushtaq, a security researcher at FireEye. The bugs were in the Java plug-in used in all the major Web browsers, including Google Chrome, Microsoft Internet Explorer, Apple Safari and Mozilla Firefox. The flaws were rated critical because cybercriminals could use them to install malware capable of commandeering a computer. Apple's patches automatically deactivated the Java plug-ins in browsers, leaving it up to Mac users to turn them back on. Until a few months ago, Apple had handled the release of all Java updates. Now, customers can download and install fixes directly from Oracle. [Bill Brenner in Salted Hash: 4 Flaws - Fun with iPhone, Java, Dropbox and the brain] "Apple is trying to distance itself from Java in general," said Marcus Carey, a security researcher at Rapid7. "Over the last six months, Java has been a headache for everyone in the industry." By turning off Java by default, Apple is making customers choose whether to take the risk in running the browser plug-in. "People who need Java are going to be on their own," Carey said. The recent outbreak has led many security vendors to advise people to disable Java in browsers, because the technology is not used on the majority of websites. Over the last few years, Java applets have been replaced with more modern Web technologies, such as HTML 5, XML and JavaScript. "In my opinion, most Apple users should just turn Java off," Andrew Storm, director of security operations for nCircle, said by email. "Apple doesn't ship it pre-installed anymore and most Java applets are slow and clunky. It's always good security practice to turn off anything you don't really need." While Apple moves away from the technology, Java remains a headache for Oracle. Many security experts have criticized the business software maker for the amount of time it takes to release a patch for known Java vulnerabilities. In the latest incident, Polish company Security Explorations said it told Oracle about the flaws in April. Oracle has not commented on why it took four months to release a patch. "Why talking to your customers about security is so difficult is beyond my comprehension," Storm said. "All software has bugs, customers know that. We don't ask for a lot of information; the minimum requirements include an estimate of when a fix will be available and some mitigation advice. How hard is that?" For years, Apple faced the same criticism for taking months to release to its customers Java updates already available through Oracle. In June, Apple appeared to change, releasing a Java patch the same day as Oracle for the first time. Apple doesn't comment on product security. "Overall, Apple has been very fast in coming out with new versions of Java, which is a great security improvement over the past," Wolfgang Kandek, chief technology officer for Qualys, said by email. Apple's response to Java vulnerabilities changed in April when 650,000 Macs worldwide were infected with the Flashback malware that exploited a Java flaw. Apple did not release a fix for six weeks after Oracle, giving cybercriminals plenty of time to build exploits and launch attacks. Click here for complete article. MacBook SMC Firmware Updateby Lance Putnam, smalldog.com  One common issue that we hear about — "faulty MagSafe adapters" — stems directly from purchasing the new ones for pre-2009 machines. In certain cases, the adapter will not power the machine at first, and thus, appears faulty. The solution is yet another example of why you should always keep your software up-to-date. Pre-2009 Mac portables use the original style MagSafe adapter, which is a small rectangular block at the end of the cable. In 2009, it was redesigned to the current form factor — the "L-Shaped" design. If you try to charge a pre-2009 machine with this adapter, and if the software is not up to date, it will not work. This is because the SMC, a micro-controller on the logic board that controls the power functions on the computer, does not know how to use the new adapter. Fortunately there is a free software update called "SMC Firmware Update." To install the update, go to the Apple menu at the top left of your screen. Select "Software Update" and install all updates. Note that if you are not able to power the machine on, you will need to use a charged battery or find a pre-2009 MagSafe adapter in order to install. Click here for complete article. Adobe releases six critical patches for Flash, AIRby Jeremy Kirk, IDG-News-Service:Sydney-Bureau - Aug 22, 2012 Apple's iWork suite may have been updated to add Documents in the Cloud support, but those weren't the only Apple-built apps to get a Mountain Lion-inspired refresh on Wednesday. Apple unleashed a spate of software updates aimed at taking advantage of features in the newly unveiled OS X 10.8. Adobe Systems released fixes on Tuesday for six critical vulnerabilities affecting its Flash multimedia application and AIR runtime, five of which could allow for remote code execution on a system. The updates affect Windows, Mac, Linux, Google Chrome and users of Android 2.x, 3.x and 4.x devices, Adobe said in its advisory. The patches address four memory corruption vulnerabilities—CVE-2012-4163, CVE-2012-4164, CVE-2012-4165 and CVE-2012-4166—and an integer overflow vulnerability, CVE-2012-4167. Also fixed is a cross-domain information leak vulnerability, CVE-2012-4168. "These updates address vulnerabilities that could cause a crash and potentially allow an attacker to take control of the affected system," Adobe said. Windows and Mac users should use Flash version 11.4.402.265, and the up-to-date Linux version is 11.2.202.238. For Adobe's AIR runtime, which allows Web applications to perform functions outside of a Web browser, Windows and Mac users should move to version 3.4.0.2540. Last week, Adobe pushed out a fix for Flash for CVE-2012-1535, which the company said had been used in limited attacks. The problem can cause Flash to crash, or, at worst, allow an attacker to take over control of the computer. The attack is initiated by sending targets a malicious Word document, which contains an exploit targeting the ActiveX version of Flash for the Internet Explorer browser on Windows, Adobe said. Security vendor Symantec wrote on Tuesday that it had detected and blocked more than 1,300 attacks since Aug. 10 using the vulnerability. Click here for complete article. Remains of the Day: Live long and prosperby Dan Moren, Macworld.com - Aug 24, 2012 The latest update to Mountain Lion may restore some MacBooks' battery life, but the OS can also stop certain applications in their tracks. Meanwhile, Facebook's iOS app gets a new lease on life, thanks to the injection of some native code. The remainders for Friday, August 24, 2012 have infinite diversity in infinite combinations. Mountain Lion update can improve battery life for some Mac notebooks (Ars Technica) If you've been experiencing battery life issues since installing Mountain Lion, you may want to consult a physician—or, possibly, install the 10.8.1 update that dropped yesterday. According to Ars, some users say that the latest version of OS X has increased portable battery life, while others just claim that it's revitalized their computers, restoring the MacBook's healthy sheen. Exceptional Apps (Red Sweater Blog) Developer Daniel Jalkut uncovered an OS X capability that allows Apple to code exceptions in OS X for specific applications. Jalkut discovered the ability while trying to launch an older version of VMware Fusion on Mountain Lion—it turned out the two pieces of software no longer played together nicely. In theory, though, this could be abused by Apple for malicious purposes—such as playing a raspberry sound effect every time you launch Google Chrome. Under the hood: Rebuilding Facebook for iOS (Facebook) Facebook software developer Jonathan Dann explains the under-the-hood changes in the latest revision of the Facebook iOS app. Long story short, the new version relies more on native iOS code than previous versions, which emphasized HTML5 Web views. Using native code has significantly improved performance in the app, making it that much faster to scroll past your friends' constant engagement and baby announcements. Click here for complete article. HP Printer Drivers v.2.11 for OS Xfrom Apple About HP Printer Drivers v.2.11 for OS X This download includes the latest HP printing and scanning software for OS-X 10.8 Mountain Lion, OS-X 10.7 Lion, and Mac OS-X 10.6 Snow Leopard. Click here for complete article. News, Info and StoriesDefault folder changes in Mountain Lionby Ted Landau, Macworld.com - Aug 17, 2012 1:30 pm Apple wants you to use iCloud as the location for your saved documents. If you aren't willing to cooperate, Apple applies some pressure to get you to change your mind. Case in point: The Open and (especially) the Save dialogs for apps that support OS X 10.8 Mountain Lion's new Documents in the Cloud feature (also called iCloud Document Library). Apple has changed the rules here, as compared to how things worked in previous versions of OS X. When you select to save a new Untitled document, the Save dialog opens with a folder location already selected. In OS X 10.7 Lion and all prior versions of OS X, if you've never changed this default location, it's probably your Documents folder. If you do change the folder location, the app typically remembers your decision. This means the next time you attempt to save a new document, the default folder will be the location you last chose. This is what most users want and expect. So far, so good. 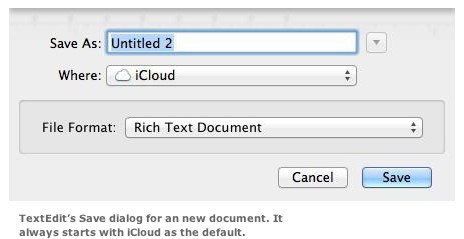
Starting in Mountain Lion, apps that support the new Documents in the Cloud feature make iCloud the default location for saving a new document. Apple is making a not-so-subtle suggestion here. I'm fine with that. The problem—at least it's a problem from my perspective—is what happens if you change the folder location. Nothing happens. The next time you try to save a new document, the default folder will once again be iCloud. No matter what you do, it's always iCloud. If you don't want to use iCloud, this means you have to remember to shift the location every time you create and save a new document. Note: This iCloud restriction applies just to saving new documents. Saving an already saved document, or using the Duplicate or Save As commands, continue to work as expected: They save to the location where the file currently exists. Further, if you know that you never intend to use iCloud for storing documents, you can disable the feature by unchecking Documents & Data in iCloud's System Preferences. This should avoid having apps save to iCloud by default. Applications that support this always-iCloud feature include Apple's own TextEdit and Preview as well as third-party apps such as iA Writer. This is apparently an OS X imposed standard that will likely spread across most apps as they begin to adopt Documents in the Cloud. If you're thinking that the venerable Default Folder X (St. Clair Software; $34.95) can help here, you'd be wrong—at least for the moment. On my Macs, with Default Folder X installed, the default location for saving a new file (when using one of the apps noted above) changed from iCloud to Documents. Oddly, in what I assume must be a bug in Default Folder X, the option to save to iCloud no longer appeared at all! In any case, the Save dialog still refused to shift the default folder to a new location—even with Default Folder X installed. That is, after selecting to save a document in a location other than Documents, the Save dialog returned to Documents the next time. Even using Default Folder X's option to assign a default folder had no effect. (Technically, it occasionally seemed to work, but inevitably reverted back to Documents after a few tries). When opening files from these apps, Mountain Lion handles the task somewhat better. You can choose to see files either in iCloud or On My Mac. Either choice is remembered the next time you select Open. If you chose On My Mac, Documents is the default folder selected. In this case, if you select a different location, it is remembered the next time you select Open. However, if you temporarily switch to iCloud for any reason, the default location reverts back to Documents when you return to On My Mac. Default Folder X also appears to work better here; I could successfully assign a default folder location via the utility, although it would not override the shift back to Documents when toggling between iCloud and On My Mac. I asked Jon Gotow, the developer of Default Folder X, about all of this. He replied: "Default Folder X enforces your default folder selection the first time a file dialog is presented by the application, but subsequent dialogs are left up to the application." The fact that Default Folder X is no longer affecting the "first time" choice "is a change that Apple's done in Mountain Lion. Mountain Lion and iCloud are basically overriding all other settings, even if Default Folder X tries to dictate otherwise." Needless to say, Jon is working on an update that will address these matters. Click here for complete article. Mountain Lion's Save As isn't what it once wasby Christopher Breen, Macworld.com - Aug 8, 2012 Reader Edward Bennett is rightfully confused by a Mountain Lion feature that isn't what it appears to be. He writes: I'm a long time Mac user and, when I upgraded to Lion, was dismayed to find that the Save As command had disappeared as it was something I used all the time. When the command returned with Mountain Lion I was thrilled but, from what I can tell, it doesn't work the way it once did. Can you clear up my confusion? Yes. Like you, I turned backflips when I saw that I could invoke the command in supported applications simply by selecting File, holding down the Option key, and choosing Save As. But that joy soon turned to gloom. For this reason: Back in The Day, when you created a document, banged away on it for a bit, saved, banged away a bit more, and then chose Save As, you created a new document that included all the changes you'd made up to that point. The original file closed and the Saved As document remained. If you opened the original later, you'd find the content it contained up to the point where you invoked the last Save (not Save As) command. The beauty of Save As from my perspective was that I could work on a story, make a few edits, and then take what I thought might be an interesting departure. If I then determined that departure might be ill-advised I could select Save As and have a greater sense of security knowing that I could always return to the original version. That is not how Mountain Lion's Save As command works. Instead, when you invoke Save As, it saves both the original file as well as creates a new one. So, in the example above, if I'd taken that departure (wiping out old content and adding new) and then chosen Save As, the content of my original file would be saved up to the point of the Save As invocation. 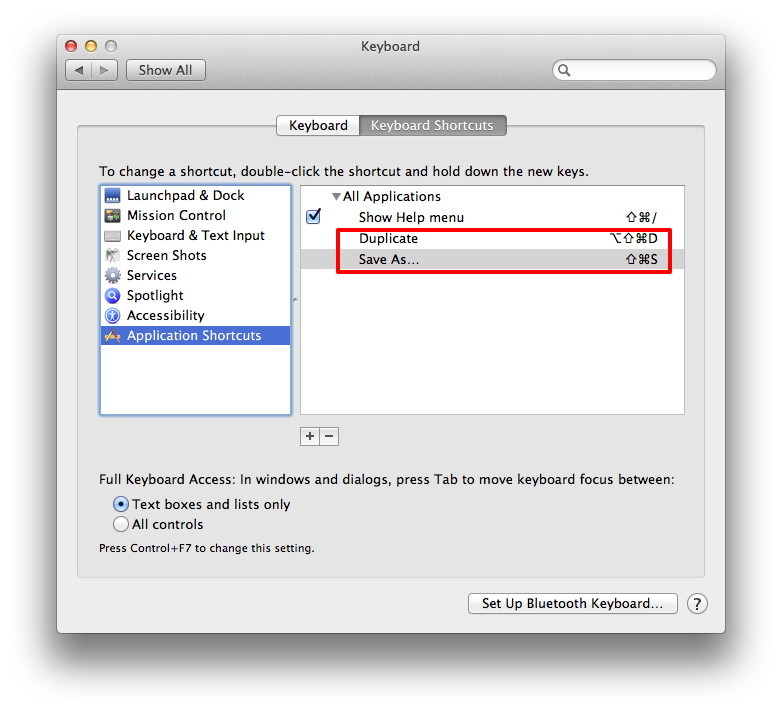
The original version's not gone, however. With Mountain Lion's Auto Save feature you can click on the Auto Save triangle in the document's title bar and choose Browse All Versions (or choose File -> Revert -> Browse All Versions). In the Time Machine interface that appears, return to the first iteration of the document to find the original original. I'll now give you a little time to wipe the spittle off your display that resulted from your "Are you frickin' kidding me!? I'm a savvy enough Mac user that I can do that, but what about the poor shmoes coming to the Mac for the first time thanks to their easy-does-it iOS experience?" ejaculation. I agree with those who suggest that the original Save As implementation wasn't entirely intuitive. But it was what we were used to and to restore the name of a command with that kind of history but change its functionality is curious to me. So, other than choosing to revert the document via the Time Machine interface, is there some other way to approximate the Save As behavior of old? Not in as few steps, regrettably. Try this: Launch System Preferences and in the General preference enable the Ask To Keep Changes When Closing Documents option. Close System Preferences. Launch the application you want to work with and do something. Save the document. Edit your document and add more content—delete some words and add a couple of paragraphs, for example. Choose File -> Duplicate (Shift-Command-S). You will now have two identical documents open. Close the original document. Because of the option you enabled in the General system preference you'll be offered the option to revert your changes, thus giving you a saved version of the original copy. Fine, fine, another spittle break. So, what we're after is a single command that invokes these steps: Duplicate, Close, and Revert Changes. AppleScript might be an option, but not all applications are scriptable (Preview, for example). I've solved the problem by turning to Stairways Software's $36 Keyboard Maestro. This is a fine macro utility (remember those?) that allows you to trigger a gang of actions with a single keystroke. Specifically, I created a macro that performs the following actions:
Yes, it's a $36 solution to what shouldn't have been a problem in the first place, but it works with any application that supports Mountain Lion's new Save As implementation. Click here for complete article. Get rid of harmful browser cookies with Cookie Stumblerby Shelly Brisbin, Macworld.com - August 17, 2012 When the Web was young, experts generally advised that browser cookies were harmless. That was before detailed user tracking across multiple sites and aggressive advertising targeting. You may appreciate the cookie that logs you into Amazon.com automatically, but you might be less eager to share your browsing habits with companies building detailed user profiles. Cookie Stumbler Standard (Mac App Store link for Cookie Stumbler Basic) finds browser cookies, including advertising and tracking ones, and gives you the option to delete them all, or inspect and banish them individually. 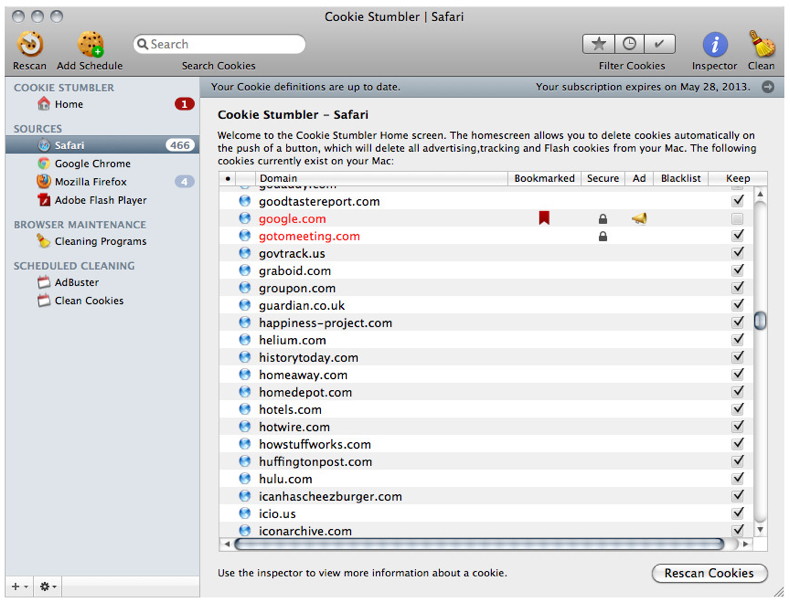
Like antivirus software, Cookie Stumbler combines an application with a subscription to regularly updated definition files. These definitions identify known advertising and tracking cookies, and delete them, based on your preferences. Cookie Stumbler currently supports ten browsers, including Safari, Mozilla Firefox, Google Chrome, iCab, and OmniWeb. It also scans Flash cookies set by Adobe Flash Player; flash cookies are not removed by a browser cleaning, even if Flash was invoked by a website. The first time you run Cookie Stumbler, it scans your Mac for browsers and their associated cookie databases, reporting back all of the cookies it finds and suggesting which ones are undesirable. You can follow its recommendations, and scroll through the complete list to inspect all cookies found on your Mac. Cookie Stumbler notes each cookie-setting domain's status; bookmarked, secure, advertising-related. blacklist, or keeplist. The blacklist and keeplist settings are suggested by Cookie Stumbler when it scans. You can override each one manually, if you wish, or double-click a domain to see what Cookie Stumbler's site advisor feature has to say about it. An inspector gives you even more information about the domain's cookies. If you're way into cookies, the inspector is quite useful, giving you a window into exactly what each cookie is doing. Since new cookies are generated almost every time you browse the Web, the best way to clean your system is to schedule Cookie Stumbler scans at regular intervals. You can choose cleaning actions based on cookie types, and set them to run daily, weekly, monthly, or at other regular intervals. The value of this "set it and forget it" approach to cookie cleaning becomes clear as the number of cookies mounts. Cookie Stumbler is for people who are both concerned about their privacy online, and interested in understanding the sources of the many threats. Click here for complete article. Getting started with WordPressby David Daw, PCWorld - Aug 20, 2012 If you need to establish a professional-looking website without shelling out cash for a Web design team, check out the free open-source blogging tool WordPress. Chances are good that many of your favorite websites use this popular platform, since WordPress makes creating and editing content on a blog incredibly easy. While the basic management tasks are simple, customizing WordPress to meet your needs can be more complicated. Over the years WordPress has developed streamlined tools for setting up a blog and customizing its appearance, but those tools don't always allow advanced users to access all of the features that WordPress offers. To that end, we've collected tips for setting up a fresh WordPress blog tailored for both beginners and experts to help you get the most out of your new website. Set up WordPress Although WordPress is technically an open-source content management system for websites, the WordPress team also allows anyone to try out the tools by creating a free ad-supported blog at yourblogname.wordpress.com. The simplest way to start using WordPress is to sign up for this kind of blog on the WordPress website; if you want a different URL, however, you can pay for a subscription that gives you a blog at the domain name of your choice, hosted on WordPress servers. If you're an advanced user, and you already pay for hosting at another service (or if you run your own domain server), you can simply set up WordPress on your personal server by downloading the open-source WordPress software from the WordPress Organization website. Whether you sign up for a free WordPress blog or install WordPress on your personal server, you need to learn how to navigate the WordPress content management system. At its core WordPress relies on a system of templates that allow you to make quick website design changes without losing any data, but advanced users who install WordPress on their own servers can access a few extra features that aren't available to users who start a free blog on WordPress.com. For example, it's impossible to install WordPress plug-ins on a free WordPress.com blog. And although you can customize a free website's layout, you can't install your own custom template; instead, you're limited to using one of the 200 or so templates that WordPress has chosen for you. Overall, WordPress.com is great for people who are just getting started with blogging. WordPress.com's free service lets you become acquainted with WordPress, and its paid-hosting service is a viable (though certainly not perfect) option for users who don't already have a domain host. If you do have a hosting service, you'll probably want to install and use WordPress on that company's servers. You may wish to poke around in your hosting service's settings before starting a full WordPress install, however, because most contemporary hosting services can automate the process for you (I told you it was popular). Hosting services typically call such features One-Click WordPress Installs or something similar, and usually they automate the steps I'm about to discuss. Advanced users: Installing the WordPress platform is not a particularly complicated process, but it does require you to make some changes to WordPresss setup files in a text editor, as well as to use an FTP client. First, you should download the latest stable build of WordPress and unzip it onto your computer. Then, you need to create a MySQL database on your server so that WordPresss PHP has a database to interact with. Remember that your Web host likely has tools to help automate this process, but such tools (and the best ways to use them) will vary from host to host. Next, you have to rename the file wp-config-sample.php to wp-config.php and edit it. For starters, you need to enter the name, admin name, and password for the MySQL database you just created; WordPress.org has a handy guide to all the changes you should make to the file. Once you have properly edited your wp-config.php file, you have to use an FTP client to upload the entire WordPress folder to your server. When all the files are in place, point your browser to http://yourdomainname/wp-admin/install.php to access WordPresss automated installer. WordPress will finish the install process itself. It should then send you to a page that allows you to name your new WordPress blog and create an administrator username so that you can start customizing the blog.  
Customize your WordPress installation WordPress has an Appearance tab devoted to letting you alter the look of your blog. Navigate to the first section under Appearance -> Themes, and choose one of the many free layouts. Keep in mind that you aren't locked into that exact appearance, since you can alter themes. Certain items are easier to adjust than others, though: In general, the color and style of the text and backgrounds are easier to change than images are (and in turn, all of those elements are much simpler to change than the layout of the template). You're better off selecting a template whose elements are generally well positioned and then making changes to the overall look of the site, rather than picking a template that has an attractive color scheme but requires significant layout reorganization. Once you've found a theme you enjoy, the easiest way to adjust it is to choose Customize. The tools that WordPress gives you will allow you to alter some aspects of the site, such as the color scheme and background image, without having to dig into the coding that makes your theme operate. Naturally, more-thorough alterations (trying to switch out a border element, for instance) may require you to roll up your sleeves and get coding. If you're not ready to tackle that challenge yet, check out our guide to learning to code for free. Advanced users: You don't have to leave your control panel to make changes, since WordPress also has a built-in theme editor (located under Editor in the Appearance tab) that lets you directly alter the coding of any part of your template. You have a great deal of control over every aspect of your blog's appearance; if you aren't careful, though, you can damage the functionality of your blog. WordPress is built with a combination of HTML, CSS, and PHP, so you should have at least a passing familiarity with all three coding languages before you start directly altering your site template. Most users should stick to changing their site's HTML and CSS, as that approach allows you to control the site's appearance yet gives you the ability to change the code back easily if you make a mistake. The most dangerous parts of a WordPress site to alter are the PHP scripts, which control the positioning of your blogs content, along with where in your database that information comes from. Mistakenly altering or deleting these scripts can prevent your blog from displaying your sites content properly, and that can turn your audience away in droves. Even so, steering clear of these sections denoted by tags is fairly easy if you're careful with your edits. Although WordPress can seem intimidating at first, the key is to change only what you feel comfortable altering. Website designers at all experience levels can run into trouble with some of the subtleties of WordPress, but even users who have no familiarity with HTML or CSS can install and customize their own WordPress blog. Click here for complete article Quick test for Macs to run Mountain Lionby Daryl Thomas, MAGIC Here is a quick test with a Terminal command to find if your Mac is Mountain Lion compatible. Open your Terminal application and type (or copy and paste): If Terminal returns a EFI32, then you have a 32 bit machine not compatible with Mountain Lion. EFI64 is ok. Or you can check this MAGIC July Newsletter article which has a list of the Macs that Mountain Lion will run on. Create calendar events more efficientlyby Christopher Breen, Macworld.com - Aug 29, 2012 Reader Caroline Anders finds Calendar's default settings a little inflexible for her tastes. She writes: I use Calendar on my Mac running Mountain Lion (and used iCal before it) and I find I have to fiddle with events after I create them—changing all-day events to events that last a couple of hours and changing their start times. Is there a better way to create events so I don't have to spend so much time editing them? There is. First, it's important to understand how Calendar creates events. If you double-click on a date when in Month view, you will create an all-day event by default unless you enter a time or specific event in the New Event field. For example, Meeting with George 3PM or Lunch with Dan. Otherwise you'll have to edit the event if your intention was to create an event that lasts just an hour. If you want just that hour-long event, change to the Week or Day view and then double-click on a time. An hour-long event will be created at the time you chose. Although a lot of us are accustomed to double-clicking on dates or times to create events, it's worth your while to check out the Create Quick Event feature. Just press Command-N or click on the Plus button at the top of the Calendar window and enter an event along these lines: Lunch tomorrow Dan. Do that, press Return, and a new event with that very title will be created at noon on the following day. Try Dinner tomorrow Dan and an event is created for 8 PM. 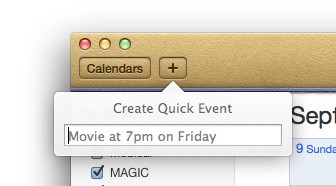
Calendar is smarter than iCal in this regard, but not as smart as Flexibits' $15 Fantastical. With Fantastical you could enter Lunch tomorrow 1 - 3 Jason San Francisco and Fantastical will create an event exactly along those lines, making San Francisco the location. Calendar, on the other hand, will get the time right, but will make San Francisco the name of the event rather than lunch and won't add the location. If you'd like to change the default alert time for timed events as well as all-day events, you can do that within the Alerts tab of Calendar's preferences. Choose an Account (iCloud, for example) from the Account pop-up menu, and configure the Events and All Day Events pop-up menus. For example, rather than the usual 15-minutes-before default, you can can choose from a number of options including 30 minutes before, 1 hour before, 1 day before, or 2 days before. All-day events are more limited, allowing you to choose On Day of Event (9 AM), 1 Day Before (9 AM), 2 Days Before (9AM), or 1 Week Before. Click here for complete article. Java security threats: What you need to knowby Rich Mogull, Macworld.com - Aug 30, 2012 First, the bad news. Once again, Mac users are at risk due to a flaw in Java, similar to the one that enabled the Flashback Trojan. Even worse, there isn't (yet) a patch to fix that vulnerability. But don't worry: This time around, there's good news for Mac users: Thanks to changes Apple has made, most of us are likely to be safe from this threat. That said, although you likely aren't at risk today, it is clear that Java still represents one of the biggest, most persistent security problems face users of all operating systems. So I recommend you consider implementing the precautions suggested below. What happened On Sunday, August 26, security vendor FireEye published information about a new Java attack that used a previously unknown Java vulnerability. The attack, which originated from China, affected the latest version of the Java Runtime Environment (Java 7, version 1.7). The attack comes through your Web browser when you browse to a malicious site and allows an attacker to silently take complete control over your computer. After FireEye's initial post, details about the vulnerability quickly became public and exploits taking advantage of it appeared in multiple attack tools. Further research by security vendor Immunity Inc. indicated that the active exploit actually took advantage of two separate unpatched Java vulnerabilities (what we, in the industry, call zero-days). The exploit for the first vulnerability was quickly added to the BlackHole exploitation kit—one of the most widely used malicious hacking tools. The exploit is also now available as an attack in the Metasploit penetration-testing framework, which is freely available and favored by script kiddies and security professionals (myself included) throughout the world. At this time, Oracle—which inherited Java when it acquired Sun Microsystems—has not commented on the exploits, although we now know that the company knew about the vulnerabilities since April and was planning to release a patch in its October update. Only time will tell if the company will break its quarterly patch cycle and release an emergency update sooner. (My money is on early release.) In summary, we have at least two exploitable vulnerabilities affecting anything running the latest version of Java, both are being used in active attacks, and one is bundled with one of the most popular bad-guy toolkits on the market (BlackHole) and a very popular (and free) security testing tool. You can't patch either one. It's the very definition of "bad". Why most Mac users aren't at risk All that said, there are two reasons why Macs are less at-risk than people on other platforms, despite being easy to exploit if the right conditions are in place. The first, and most important, reason is that relatively few Macs are running the vulnerable version of Java. Any operating system running JRE 1.7 is affected, but the attack doesn't work against JRE 1.6. That last one is the version that Mac users have installed (assuming they use Java at all). The only way to update from Java 6 (1.6)—the last version supported by Apple—to Java 7 is by manually downloading and installing it from Oracle. And apparently few Mac users have done so: For example, according to a representative of Crashplan, the online backup service that uses Java for its client app, none of that company's users (who must have Java installed) are using the vulnerable version. The second reason you don't have to worry, even if you do have Java 7 installed, is that Apple by default disabled Java applet support in Web browsers in its most recent Java security update. Starting with OS X 10.7 Lion, Java isn't installed by default anyway. And even if you do turn on Java, OS X will turn it off again if you don't use it for a while. Many users do install Java for websites or applications (like Crashplan) that require it. But, again, even if you did install Java, the odds are very, very good that you aren't running a vulnerable version. What you should do There are two simple ways to check to see if you're vulnerable to this latest threat. 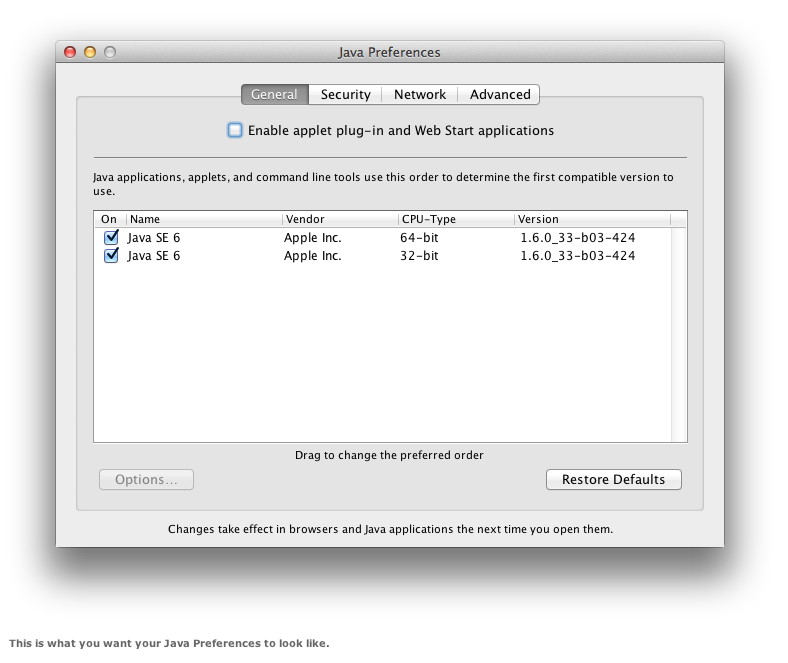
The first option is to run the Java Preferences app (/Applications/Utilities/). On the General tab it shows the version of Java you have installed. If it says you're running Java SE 7, and if the Enable Applet Plug-in and Web Start Applications option is checked, you are exposed. If it says Java SE 6, or if that applet option isn't checked, you're safe. You can also check your version by opening Terminal and typing java -version. This time you want to make sure the response isn't 1.7. If it is, don't be too alarmed; you can't be exploited if you don't also have that browser support turned on in the Java Preferences app. If you are vulnerable, immediately uncheck that Enable Applet Plug-in and Web Start Applications option in the Java Preferences app. Doing so isn't a perfect defense, but it does prevent malicious websites from exploiting you. ( You could still be tricked into downloading an exploit that you would run manually.) Using the Java Preferences application is more reliable than disabling Java in your browser since it blocks it from all browsers at once. This allows you to still use Java on your Mac, but without the risk of being infected through your web browser. The safest way to keep using Java If, like me, you still need to use Java in your web browser, I recommend the following steps. They will reduce your risk, and I recommend them as an ongoing security practice even if you aren't on the vulnerable version of Java. Because, to be honest, these Java attacks aren't about to slow down anytime soon. First, manually disable Java in your Web browsers. Even if you turned it off in Java Preferences, this will keep it from running if you ever change that setting (which we are about to do). In Google Chrome type chrome://plugins in the address bar and click the link to disable Java. In Safari, go to Safari > Preferences and uncheck Enable Java on the Security pane. In Firefox go to Tools > Add Ons > Plugins and uncheck Java Plug-In. Next, re-enable Java applet support in the Java Preferences application (or wait for your Mac to automatically prompt you the next time you need it). Third, pick a secondary browser that you never normally use and re-enable Java in it. For example, I use Chrome as my primary browser, and I disabled Java in it. I almost never use Firefox, but I still have it installed and Java is enabled in it. This protects me as I browse around the Web. (I also use Safari for development testing, so I keep it disabled on that). Whichever browser you choose as your secondary one, you should use it only when you know you need to use Java and you are going to a website you know. For me, I mostly need Java for presenting webcasts, so when I hit a site I must use that requires Java, I use my backup browser. Disabling Java in your day-to-day browser and having a second browser for Java needs isn't perfect, but it does offer a lot of protection. It's easier to remember than installing a tool like NoScript which blocks Java on individual pages, but which many non-techie users find cumbersome. (I actually run it in Firefox, as another layer of protection, but I'm a raging security geek). Another option is to access Java sites only from inside a virtual machine. I run VMWare Fusion () (and sometimes Parallels Desktop []) and frequently use Windows virtual machines for visiting those non-Mac-compatible websites I sometimes need for work (again, usually old webcast systems). I keep a baseline snapshot of my virtual machines, and revert to those after any risky activity. We dodged a bullet For once, being a software version behind worked to the advantage of Mac users, and nearly no Mac users are really at risk from the latest Java exploits. But, as we've seen with Flashback and this recent attack, Java remains a prime target. Thus I'd recommend that all users protect themselves, even if you aren't currently at risk. Disable Java if you don't need it, turn it off in your browsers if you don't need it there, or only use it under controlled circumstances if you don't have a choice. Click here for complete article. Browser plug-in and website warn about data harvesting by Facebook appsby Juan Carlos Perez, IDG News Service - Aug 31, 2012 Secure.me has developed a website and a browser plug-in designed to make Facebook users aware of the personal information that gets harvested by third-party applications. The App Advisor Security Network website has profiles on more than 500,000 third-party Facebook applications that describe the user data they collect, what actions they can take and whether they are considered unsafe. The application profiles also display user ratings. Meanwhile, the App Advisor browser extension, which works with Safari, Firefox and Chrome, gets activated when users visit either application sites or call up an application's page in the Facebook App Center. In those instances, the browser extension displays a pop-up alert that informs users of the reputation level of the application and gives them the option to call up more detailed information. The browser plug-in will be available on Wednesday. The goal is to inform users about potential privacy risks associated with linking third-party applications with their Facebook profiles. Click here for complete article. "Hidden" Wi-Fi Diagnostic Toolby Juan Carlos Perez, IDG News Service - Aug 31, 2012 
In my internet wanderings I discovered a few articles pointing to a mysterious Wi-Fi diagnostic tool that Apple snuck into Mountain Lion. A common reason people check machines into our service department relates to perceived poor Wi-Fi service, so I wanted to share this with our readers. This tool is available for anyone running 10.7 or later. The tool is slightly different for Lion users than it is for Mountain Lion users. If you're running Mountain Lion (10.8) hold down the option key on your keyboard and click on the Wi-Fi icon in your menu bar. It's the one that is pie wedge shaped. You'll see a menu item called "Open Wi-Fi Diagnostics." If you're running Lion you'll need to navigate to it manually by going to the following folder: /System/Library/CoreServices. As with most applications you don't want to move it from it's original install location, so do not move the application from that folder! If you want to make a shortcut to it to keep somewhere else that's fine. (MAGIC Editors note: In the CoreServices folder there is a file titled NetworkDiagnostics.app, but the file this article refers to is titled Wi-Fi Diagnostics.app.) If you're on Mountain Lion press Command+N to open a utilities window and then click on "Wi-Fi Scan." For Lion users you'll want to use the Monitor Performance tool. Both will give you the list of available networks as well as their signal and noise information. Here's a trick on how to get to folders that are hidden: Within Finder, go to the Go menu and choose Go to Folder. In the window that opens up, enter the following: /system/library/CoreServices This should get you to the right folder. You can also use this trick to get to your hidden personal Library folder. Just enter: ~/Library Here's some information from Technorati on how to tell if you have a good signal: "The 'Signal' number specifies the signal strength between your Mac and the Wi-Fi access point or router. The higher this number is, the better. But note that these are negative numbers so a Signal of -60 is higher (and stronger) compared to a Signal of -80. The Noise number represents the amount of wireless noise that can interfere with the Signal. In this situation, we want lower numbers. So again, because we have negative Noise numbers, a Noise level of -94 is better than one of -90. Finally, we can take the Signal and Noise numbers to come up with a Signal-to-Noise ratio (SNR) for our wireless connection. So for example, If I have a Signal level of -60 and a Noise level of -91, the difference between these two numbers is 31. The higher the SNR is, the better the Wi-Fi performance will be. Typically a SNR of 25 or higher will give you great Wi-Fi performance." Click here for complete article. One Player to Play Them Allby Nathan Poirier, smalldog.com 
Back in the olden days of computing (6 or 7 years ago) playing a particular video on a Mac could sometimes be quite a challenge. In order to play a certain type of video file, you would need a specific video player to go with it, and in the computing world there are many, many different video formats! There's Flash Video, Raw DV, Windows Media Video, Real, MPEG 1, 2, and 4, DivX, AVI, Matroska (MKV), Xvid, 3ivX, and many others. All of them would either require a special player or a particular type of "codec" (coder/decoder - kind of similar to a plugin) in order for your computer to know how to translate that video file into something that you could actually watch and enjoy. On the Mac, OS X tends to stick to a small handful of video formats, all of which QuickTime does a pretty good job of working with. However, if any of you readers out there have friends with Windows-based PCs, or even certain brands of video cameras, you may be aware that playing videos that they send you is not always an easy task. This is where something like VLC Player comes in. VLC Player is a lightweight, free, and open source application that has the ability to read just about any common video format in the known computing world. Not only can it play all of the video formats that were mentioned previously (and more!), it also has the ability to play from streaming video sources as well as close to two dozen different audio formats. While the latest version of VLC for Mac requires an Intel based Mac and OS X 10.5 or newer, if you have an older computer (even one that is PowerPC based) you can still find versions from the downloads page that will support your machine. If you've ever found yourself stuck trying to play a video that QuickTime simply refuses to touch, do yourself a favor and try out VLC! Click here for complete article. Security in the iCloud ageby Lex Friedman, Dan Moren, Macworld.com - Aug 6, 2012 Editor's note: Mat Honan has posted a full account of how hackers gained access to his accounts and wiped out the data on his devices. Apple spokesperson Natalie Kerris told Macworld: "Apple takes customer privacy seriously and requires multiple forms of verification before resetting an Apple ID password. In this particular case, the customer's data was compromised by a person who had acquired personal information about the customer. In addition, we found that our own internal policies were not followed completely. We are reviewing all of our processes for resetting account passwords to ensure our customers' data is protected." The future is now. Our devices are interconnected, and that linking where everything can access everything is wonderful. But it turns out there's a dark side, too: All that connectivity makes it much easier for an attacker to compromise all our data, no matter where it is. Wired's Mathew Honan learned this the hard way over the weekend, as a hacker not only gained access to his devices, but also wiped all the data from them causing a fair bit of mayhem along the way. As Honan reported on his blog, he was hacked hard. And the attacker didn't use complicated algorithms to brute force his way into Honan's accounts. Instead, the hacker reportedly called up Apple's technical support line, pretended to be Honan, and successfully provided answers to Honan's self-selected security questions—the very ones Apple asks of all iCloud customers, to ensure that their accounts are secure. (We contacted Apple to confirm that account of events, but the company hasn't responded.) [Update: Honan has said via Twitter that the hacker did not provide security question answers, but rather compromised the account in a different way.] That's a technique called "social engineering," which takes advantage of what is often seen to be the weakest link in the security chain: other people. Even the most secure password in the world can be compromised if you can convince the person on the other end of a phone line that you're the account holder in question. Merely having his Twitter and Gmail accounts compromised, and the data on his iPad, iPhone, and Mac wiped out would be bad enough for Honan (who, we should note, is a former Macworld editor). What made matters worse in Honan's case was the fact that he lacked any backups for more than a year's worth of data. The take-home lesson for the rest of us, then, is that our security is multi-faceted. There are many steps you can take to keep your data secure, and some important questions you might want to consider before you sign up for new services or add new devices. Secure that password! Any password can be compromised (especially given enough time or inclination). But a secure password is still your first line of defense. Using common data like a birthday or a child's name can be guessed by anyone who has access to your Facebook profile. And yet, past password leaks have shown that many users still rely on inane passwords like '1234' or even just the word 'password.' Those are in many cases as ineffective as having no password at all. A good password has two important qualities. First, unlike the aforementioned passwords, it's hard to guess, meaning that somebody has to either trick a person into revealing their password, or perform what's called a brute-force attack—essentially, trying every possible password until they hit upon the correct one. 
Second, a good password is easy to remember. That means that it's something you can recall without writing it down—because, as soon as you have to write it down, it means that you've already compromised the security of that password. The best password is stored only in your head. So, though you might be encouraged to create a password of random alphanumeric characters, like xdK92z!, it turns out that they're not terribly secure, because they're hard to remember, and relatively simple for a computer to crack. You can add a tremendous amount of complexity to your password with a technique that ends up keeping your password fairly simple to remember: Use a full sentence. This adds an order of magnitude of difficulty for a computer to guess your password through brute force, particularly since—despite thrilling movie scenes that show passwords hacked character by character—a hacker needs to determine your entire password in one go. With a password like "Six dogs ate schnitzel in a haberdashery," instead of merely needing to pick one right word at random, or a relatively short series of jumbled characters, the algorithm would need to correctly guess seven unique words in tandem. Even just a series of random words that you can connect with a mnemonic (such as "correcthorsebatterystaple") is more secure than many randomized passwords. Passwords are not recyclable - do not reuse And as you've no doubt heard, you don't want to use the same password at more than one site. Though there are software solutions—including OS X's own built-in Keychain—that can help you keep track of multiple passwords, there's an easy way to do so on your own, too: Keep your core password the same, and add special pre- and/or post-fixes based on the specific sites or services you're using. For example, you might decide to take the first and last letter of a site's name and use them in combination with your password: "Six dogs ate schnitzel in a haberdashery" becomes "ANSix dogs ate schnitzel in a haberdashery" for Amazon, and "EYSix dogs ate schnitzel in a haberdashery" for eBay. That way, it becomes considerably more difficult for a hacker who gets access to your Amazon password to use that information to start bidding on auctions elsewhere. (The more complicated your pattern, of course, the better you're protected.) The security question question Even if you follow all that password advice, though, it's not enough to guarantee your security: Many attackers take a social engineering approach instead. Even the toughest password in the world could fall victim to a charming hacker who sweet-talks the agents on the line for customer support. You've likely noticed a trend in recent years towards more, shall we say, creative security questions from certain websites. As "your mother's maiden name" becomes overused, banks and other sites that value security have turned to increasingly esoteric questions: the city where you met your spouse, the first name of your oldest niece, or the street of the first place you lived. Some sites even provide the ability to make your own custom questions. Which can be helpful, up until two years later, when you suddenly can't remember the answer to "Why we laughed all night on that Hawaiian vacation?" In the past, hackers have even gained access to Sarah Palin and Paris Hilton's inboxes by providing the necessary (and discoverable) answers via an online form—no extra human required. A good rule of thumb is: If someone can guess or Google for the answers to your security questions, they're not very secure. This puts customers in a tough spot. Your first instinct might be to use fake answers to your security questions, since in theory an intrepid searcher shouldn't be able to guess those. But just as "xdK92z!" makes a lousy password, it's a subpar security answer, too, because it's yet another piece of data—in this case fictional—that you have to remember. One option you could consider is using a pseudo-password alongside your security answers: If your Mom's maiden name is Ellen, you might use "Ellen schnitzel haberdashery" instead; your eldest niece becomes "Claire schnitzel haberdashery." Such a secure measure should at least give a theoretical support rep pause before agreeing to an impostor's request to reset your password. Unfortunately, though, unless Apple overhauls its security policies—by implementing two-factor authentication, limiting under what circumstances or time frames it will allow a customer's data to be reset, or both—your iCloud account is still only as safe as a support rep treats it. 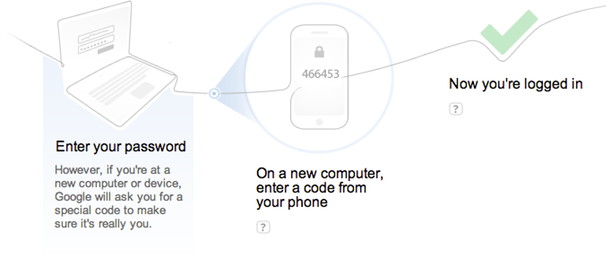
Google, for example, offers two-factor authentication as an option. When you enable it, after you log in with your password, Google sends a code to your cell phone via text message. Only after you enter that code do you get logged in. That way, an attacker needs to figure out your password and steal your phone to break into your account, and we know most nerds don't make good muggers. Consider your options Apple has been pushing iCloud hard with the release of Mountain Lion, and the company's only likely to become more insistent over time. But as great as it is to have all your documents and other information available, no matter which device you're on, it can lead to vulnerabilities, too. 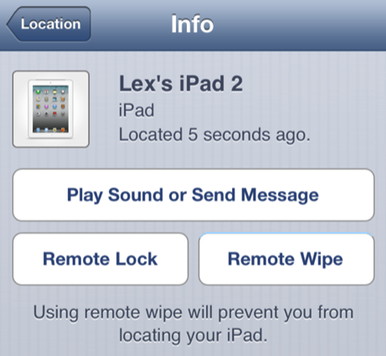
For example, the Find My iPhone service not only allows you to locate your iPhones, iPads, and Macs—which could be a potential security risk if you don't want people knowing where you are—but once you've logged into the service, you can also use it to remotely wipe data from those devices. On the upside, you can use that service to prevent someone who's stolen your physical device from gaining access to your data. On the other hand, if someone breaks into your account and remotely wipes your data, that means you'll at the very least have to spend time restoring your devices. Far more catastrophic is the case where, as with Honan's situation, you have out-of-date backups or no backups at all. Of course, that's not a reason not to use that feature, any more than worrying about sharks is a reason not to go swimming. But it's worth considering the consequences of a service before you blithely sign up for it, and it's definitely worth making sure that an account which has access to such capabilities is as secure as possible. Back that disk up It should go without saying that every user needs to have a current backup of the data on their electronic devices—preferably more than one. Data loss happens for a number of reasons, but that can include security violations. Having a remote online backup is valuable, just in case your house is flooded or catches on fire, but it's unwise to put your only backup into the hands of an online service. Had Honan's hacker been especially malicious, he could easily have deleted the iCloud Backups for Honan's iOS devices. We've written plenty about backing up, but the short short version is: Use Time Machine, sign up for a service like CrashPlan, or at the very least, save your most important data to Dropbox. Of course, no online service is bulletproof, so it's always wise to keep at least one local copy of your data, just in case. Don't panic What happened to Mat Honan was, in a word, awful. We don't want that to happen to us, or you. But while an Apple support rep may be to blame for enabling Honan's victimization, blame for the data loss—as Honan would no doubt agree—falls squarely on his shoulders. Having good backups means never worrying about your data. Couple that peace of mind with strong passwords, strong security answers, and careful consideration about the services you enable, and you needn't feel fear each time you register for a new online service or save your files to the cloud. Click here for complete article. Wizard's advice: I get nervous about putting sensitive personal data out on the web or in the cloud. How secure is it? Not 100%. Be very careful what you put out there. Robert join.me - sharing your screen for free*from Sue Keblusek, MAGIC My sister and I speak on Skype quite a lot. She recently introduced me to join.me. It allows you to see someone's desktop in real time. You may already know about it but I liked it quite a bit. Here's the link: Sue iPhones, iPods, and iPadsiPhone for the Blind, news articleby Daryl Thomas, MAGIC The September issue of Lion Magazine published by Lions Clubs International has an extremely interesting article (page 29) on how use of iPhones has made their lives so much better. It discusses the provision of Apple iPhones to the blind by Lions Clubs, and it provides a life changing experience to the recipients. The manager of adaptive services at Chicago's Guild for the Blind states that the Apple iPhone is orders of magnitude better than other smart phones on the market for this purpose. The article also says that not all organizations that provide accessibility services to the blind are fully aware yet of the iPhone's unprecedented powers. The online version is available at the link below, and I strongly recommend reading it. Be patient, it loads slowly with its own reader which worked fine on my Intel iMac running 10.6.8. Touchscreen Shortcutsby David Boyd , smalldog.com 
If you own a Mac, an easy way to increase your productivity is to memorize Apple's documented keyboard shortcuts. You can study them here. But what about your keyboard-less iPhone, iPad, or iPod; are there any touchscreen interface shortcuts? Apple has a website with you in mind. Luckily for you, I have assembled a list of my own favorites which I've found by accident in the last five years.
Click here for complete article. Photo book creation tool emphasizes the printed book experienceby William Porter, Macworld.com Pholium ReviewPholium is an iPad app designed to create virtual books of your photos. The app, in turn, is linked to an online service that lets you share your books with friends. Pholium 1.3, the newest version, includes a number of major improvements over previous versions, and a price drop to free. 
Pholium Gallery You get started with Pholium by importing some photos into Pholium's Gallery. This is not as easy as it sounds because you have to use the iOS photo picker to select photos, and the thumbnails in the photo picker are tiny. It's difficult to tell if the photo you're picking is in focus or whether the subject's eyes are fully open, for example. After dealing with this frustration through my first few Pholium books, I finally got smart and organized everything outside Pholium into a single folder. I still had to import the images one at a time, but at least I didn't have to make decisions about what to import. The Gallery provides some modest photo editing tools that let you adjust brightness, contrast, and exposure, and do a couple other minor tweaks, but Pholium is no Snapseed or iPhoto—Pholium doesn't even have a crop tool—so I recommend doing your editing before you import. Later in the process, when you place a photo on the page of a book you're creating, you have to use Pholium's photo picker to place photos from the Gallery into the pages you build. The thumbnails are still small, but the Pholium photo picker does display any stacks you created in your Gallery. It certainly would be easier if you only had to pick your photos once—when you're placing them on the page—and if you could at least crop them right on the page. 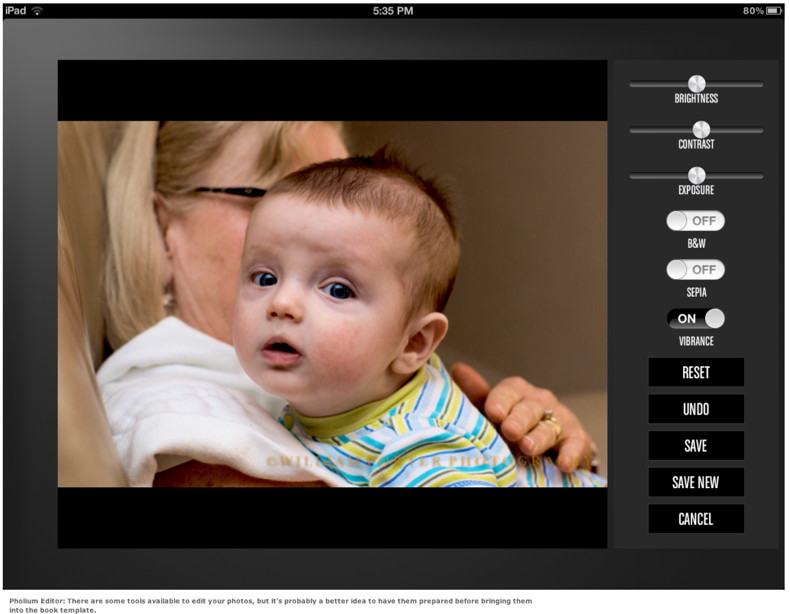
Pholium Studio Once you've imported all the photos you want into the Gallery, you're ready to make a book. You do this by moving into the Pholium Studio and clicking the New command. You can create a blank book, in which you place the images anywhere you like, or you can have the program place images on the pages for you. In that case, you'd select from one of the basic page layout options. Letting Pholium make the book for you is certainly easier, because you can select all the images for the book at once, using a large, full-screen selector reminiscent of the thumbnail view in the Photos app. Whichever method you choose, you'll be asked if you want to use the Classic or Modern style. The Classic style has been available in Pholium since version 1.0; it looks like a real book, with a faux gutter separating the left page from the right, and with soft pages that turn like the pages in iBooks. The Modern style, new in version 1.3, removes the faux gutter, and the pages seem stiff when they turn, like the pages in a Flipboard app. 
After you make these preliminary choices, you'll be looking at the front cover of a new book. Enter a title and subtitle as instructed, then open the book (swipe left) to get to the inside title page, where you enter the title again and a short preface. You can format the fonts and paragraphs for these text blocks and also adjust their placement. If you let Pholium create the book for you, the cover and inside pages of your book will be filled with photos. You can open the book and edit the placement of photos if you like. You can also add a picture to the back cover. If you asked Pholium to create a blank book, you'll have to add each photo yourself. Click the Pages button at the bottom of the screen to add a couple of blank pages, then click the Photos button to select a photo from your Gallery. Each two-page spread can have as many as four photos or as few as none (if you just want to place text). You can resize (but not crop) photos and you can rotate them. One photo can overlap another. You keep adding pages and photos until you're done. You can create as many pages, and place as many photos as you like in a Pholium book. When you're done, if you want, you can place a photo and/or a caption field on the outside back cover as well. Click Done to close the book editor and click Review to flip through what you might call the page proofs of your book. Pholium 1.3 also allows you to add text to the inside pages of your book. The tool for this is labeled Caption, but you can use a caption box to enter any text you like, from a simple title for a photo, to a short paragraph or two. As the edges or middles of two objects (photos or caption fields) get nearly aligned, Pholium displays a dynamic guideline based on the previously placed object. But you can't draw any default guidelines for pages to help get all the photos in the book aligned to exactly the same place on the page. 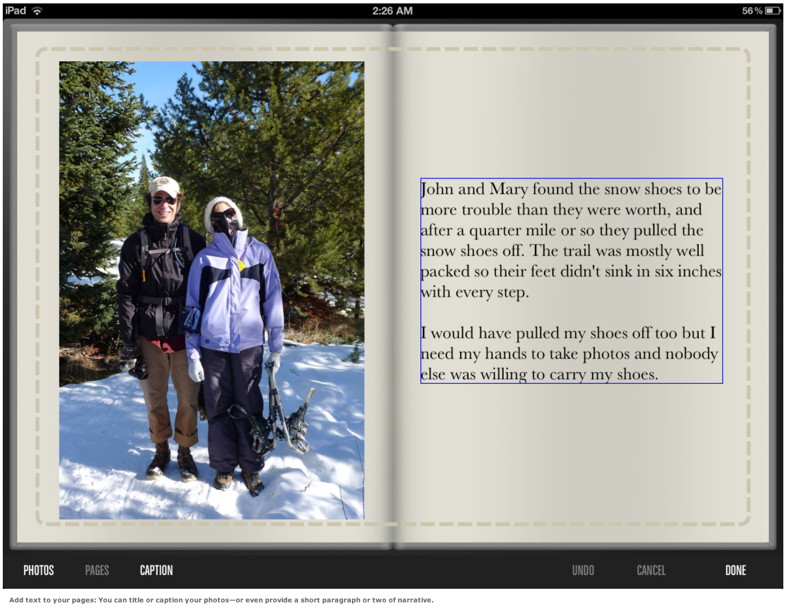
Pholium Publishing If you like what you see, you can now publish your book to your Pholium Library. Once a book has been published, you cannot edit it further. However, if you want to make a change, you can use the Copy command to make an editable copy of the book. Once a book has been published, you can send it to somebody. In fact, you can send it to as many somebodies as you like, and for free. To share books, you have to be logged in to your iCloud or Dropbox account. Unfortunately, you can only send a book to 10 people at a time, so sending a book to 100 people is a bit tedious. 
What your recipients get is a link that will let them download your Pholium book to their iPad and open it in their own copy of Pholium. What if they don't have an iPad or simply don't want to download Pholium? They'll get a link to a Web page that displays something that kinda, sorta looks like your book. Book experience Even for people who do have an iPad and Pholium, the Pholium book experience doesn't exactly match a real-world book experience. A real dead-trees book can be a book and make your photos look fantastic at the same time. Pholium can do both things, too, but not at the same time. One problem is that the page display places your photos under a layer that causes them to lose some sharpness or clarity. This is especially apparent on a retina-display iPad. Another problem is that the looks-like-a-book virtual packaging takes up screen space, and that means less area for your photos. This is particularly problematic because a Pholium page (like a normal book page) is taller than it is wide, while most photos are wider than they are tall. If you have a great landscape photo, you can let it stretch across both pages of a spread, but—if you selected the Classic book style—you'll get an ugly faux gutter in the middle of it. 
While your photos can indeed look terrific in Pholium, it's best to abandon the book metaphor. When you're looking at a photo on a Pholium page, simply tap on a photo to view it, by itself, in full-screen mode. Or click on the Slideshow button to flip through all the photos in the book in full-screen mode. Either way, the images look really nice on my retina-display iPad. Do they look any nicer than they do in a Web photo sharing service like Google+ or Facebook or 500px? Not really. But the point of Pholium isn't simply to display your photos beautifully, which you can do without Pholium, it's to provide the book experience. Worth a look Pholium presents your photos in a distinctive way, and even if you don't send your photos to anybody, making a book with Pholium is a lot of fun. It's neat to see your photos "published" in a book without having to chop down any trees. Note also that, while Pholium isn't perfect, it is still a very new app and under active development: version 1.3 is the third update in almost as many months. And, hey, it's totally free, so if you think you might be interested, by all means, give it a try. There are also alternatives to Pholium worth looking at: Blurb Mobile is pretty good and iPhoto Journals, while not exactly book-like, also provide a terrific way to package and share albums. Click here for complete article. Three painless ways to get photos off your iPhoneby Dave Johnson, PCWorld - Sep 3, 2012 Editor's Note: The following article is reprinted from the Digital Focus blog at PCWorld.com. They say that the best camera is the one you have with you. By that measure, smartphones are the best cameras around. As I've previously reported, iPhones are the number one camera used to upload photos to Flickr, and I can attest to the fact that it fits in my pocket better than my Nikon D7000. In the past, I've given you some advice on how to take better smartphone photos, which is great, but the most vexing part of using the iPhone is getting photos onto your PC. Rather than emailing photos back to your PC all the time, try one of these three handy ways to automate the process. Bump to Transfer There are two kinds of smartphone photographers: People who consider smartphone photos disposable, and mostly keep them only on the phone, and people who want all of their photos copied to the computer for posterity. 
If you fall into the first category (you only occasionally want to get certain photos onto your computer) then this solution is for you. Imagine that you want to copy a photo from your iPhone to your computer. Instead of emailing it to yourself, or some other clumsy solution, you could just tap the phone on your keyboard, and your photo would immediately be sent to its destination. To do that, you need a free iOS app named Bump. Bump was originally designed to let you share contact information with another iPhone owner by bumping the phones together. The app uses accelerometer and location data to know to exchange information with the nearby phone. But in a recent update, Bump now copies photos to the PC if you use the phone to tap the space bar when your browser is open to the Bump page. (You must use Chrome, Firefox, or Safari.) Use Dropbox Bump is great, but as I've already pointed out, it is efficient only if you occasionally use it. If you want all of your photos on your computer, there are better options. One such choice is the venerable cloud storage service Dropbox. Pretty much everyone knows about Dropbox, the site that gives you 2GB of online storage for free. It also offers oodles of opportunities to get gigabytes of additional storage without forcing you to break out your credit card. A client app makes it easy to drag and drop files to the cloud from within Windows. What many people don't know is that a recent update to Dropbox's iOS app can automatically upload all of your photos and video to Dropbox for you. All you need to do is start the Dropbox app on your iPhone or iPad and any new photos and videos will automatically get transferred to Dropbox (and therefore any PCs to which you are syncing). This is a truly amazing feature. For the first time, I can now get to all of my phone's photos from wherever I am, on whatever device or PC I happen to be using. And the Dropbox app is, of course, free. CameraSync is fully automatic 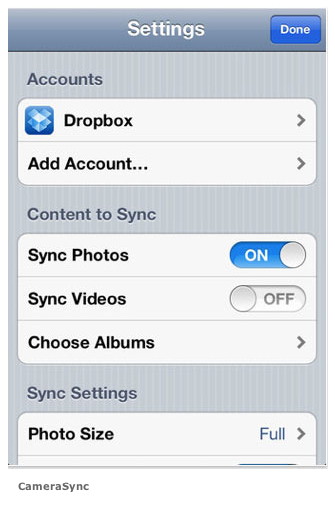
But as good as Dropbox is, you still have to start the app in order to kick off the sync. Who has time for that? That's where CameraSync comes in. CameraSync is an iOS app that takes the basic idea behind Dropbox (automatically sync your photos with the cloud) and turns it up to 11. This $3 app takes all of your latest photos and videos and copies them to the service of your choice (including Dropbox, SkyDrive, Box, and Flickr) whenever you arrive at a specific location. CameraSync relies on your phone's location services to start doing its thing. So I can specify home and work, for example, (two places with Wi-Fi) and CameraSync will place my newest stuff in Dropbox for me. In order to use the location-aware feature in CameraSync, you need an iPhone 4 or better, or an iPad 2 or newer. Click here for complete article. By The WayForm Fill Tips*by Ron Sharp, MAGIC Most browsers will remember your form entries on web pages. When you type your email address into a text field, for instance, the browser will remember it unless you have private browsing turned on. So the next time you start typing in a text field, suggestions will show. But over time you may end up with suggestions that are no longer useful. There are ways to adjust those form fill tools. In Firefox, if a number of suggestions come up when you start to type in a text field you can delete an individual entry suggestion by going down the list and highlight the one you want to delete. Then press the Shift and Delete keys. If you want to delete all the suggestions stored, then under the Tools menu on the top menu bar, click "Clear Recent History." You can also change your Firefox preferences by unchecking "Remember search and form history" from the Privacy menu. Here is a Firefox help page that has a list of tips: http://support.mozilla.org/en-US/kb/control-firefox-automatically-fills-in-forms. This Firefox page offers help for removing browsing and search history: http://support.mozilla.org/en-US/kb/remove-recent-browsing-search-and-download-history In Safari, you can adjust the form fill tool by going to Safari Preferences and selecting Autofill. For extra security it's advisable to not allow Safari to use info from Address Book, but you can edit the User names and passwords it stores. Other browsers have similar options. 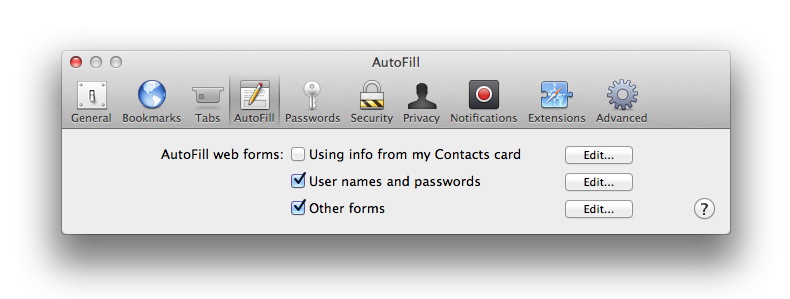
MAGIC, the Macintosh Appreciation Group of Island County, serves people who use Macintosh computers, software and peripherals. Our goal is to share information and get answers to questions to make us more productive with our use of technology. Our monthly meetings give us a chance to discuss computer problems and share ideas with other Mac users, feature speakers on specific topics, and to keep apprised of Apple news. |